Saturday, December 31, 2016
Adobe Photoshop CS5 Extended 12.0 Mac
The most common powerful tool you for photo editing now a days more feature like gif making,, flash file, internet we designing and much more finally now available for mac with patch works on 64 bit and 86 x mac OS first thing your need to download then if beginner watch tutorial to install this
Download full Apps Torrent here Download or Mirror
Tutorials:How to install
MS Office 2016 for mac Patch
Friday, December 30, 2016
deposit.com gold membership
step 1: click on this link: Deposit Files
step 2: enter one of the codes below
Code:
step 2: enter one of the codes below
Code:
n5kit65v
f94ce2cp
czse59yy
bb43hiak
d4aewku8
step 3: click send....done
step 4: No need to change email or password or login. just use it as it as.
step 3: click send....done
step 4: No need to change email or password or login. just use it as it as.
Thursday, December 29, 2016
man vs wild ecuador
finally this man begin to lose hope in this jungle where mother nature show his beauty and all greenery plants and animals most of insects survive by god gifted survival techniques while British force main main start to dying and lost hope cant find his way out to civilization even eating insects cant face his way back to home watch out.
Watch Online SD
Watch Online SD
Tuesday, December 27, 2016
Minority Report
Set in Washington D.C. in 2054, where police utilize a psychic technology to arrest and convict murderers before they commit their crime, the film tells the story of an officer from that unit who is himself accused of a future murder.
Assassin’s Creed
Through a revolutionary technology that unlocks his genetic memories, Callum Lynch experiences the adventures of his ancestor, Aguilar, in 15th Century Spain. After exploring his ancestor's memories and gaining the skills of a Master Assassin, he discovers he is a descendant of the secret Assassins society.
Lovi Os Nokia X2 Rom
Features of Lovi OS
1.Android Core by CM
2.Comes with some pre-installed apps for perfect mobile productivity
3.Compact UIX inter-platform release
4.Lovi OS also comes with ‘Kingsoft WPS office for Android’ for perfect mobile office productivity.
Working
GPS
WiFi
Hotspot
Camera
Bluetooth
Mobile data
Multi SIM
1.Android Core by CM
2.Comes with some pre-installed apps for perfect mobile productivity
3.Compact UIX inter-platform release
4.Lovi OS also comes with ‘Kingsoft WPS office for Android’ for perfect mobile office productivity.
Working
GPS
WiFi
Hotspot
Camera
Bluetooth
Mobile data
Multi SIM
Bugs
not yet found
How to flash
1.Download the zip files for your device
2.Reboot your phone to recovery mod
3.Wipe data/factory reset
4.Flash the downloaded zip file
5.Install zip
How to flash
1.Download the zip files for your device
2.Reboot your phone to recovery mod
3.Wipe data/factory reset
4.Flash the downloaded zip file
5.Install zip
Monday, December 26, 2016
Plants vs. Zombies 2 Mod APK + Data
Features
NEW PLANTS! NEW ZOMBIES!AMAZING WAYS TO PROTECT YOUR BRAIN
GET CRACKING IN VASEBREAKER
UNLOCK YOUR ZEN GARDEN
LOOK OUT! SHARKTRONIC SUB!
NEW LEVELS OF EXCITEMENT
Downloads:
Saturday, December 24, 2016
Man Vs Wild season 1 full
a US Army x solder try to teach you how to survive in hardest situation and came back home without die, this man fight with human nature and survive eat any thing for living and drink even his own pee watch season one full series discovery channel production
Watch Online SD
Watch Online SD
Tuesday, December 20, 2016
Valkyrie
The movie is a dramatization of the 20 July assassination and political coup plot by renegade German Army officers who desperately find a way to stop Hitler before Europe and Germany are destroyed.
fury 2014
April, 1945. As the Allies make their final push in the European Theatre, a battle-hardened Army sergeant named Wardaddy commands a Sherman tank and his five-man crew on a deadly mission behind enemy lines. Outnumbered, out-gunned, and with a rookie soldier thrust into their platoon, Wardaddy and his men face overwhelming odds in their heroic attempts to strike at the heart of Nazi Germany.
Saving Private Ryan
Following the Allied invasion of Normandy, a squad from the 2nd Ranger Battalion of the 29th Infantry Division go behind enemy lines to retrieve Private James Francis Ryan whose brothers have been killed in action.
Monday, December 19, 2016
Moto X - XT1085 Rom
Download Motorola Moto X 2nd gen-2014 stock rom and firmware
661.9 MB
615.6 MB
615.7 MB
636.6 MB
665.3 MB
Sunday, December 18, 2016
Supernatural - Season 12
Season 12 begins with Dean becoming overwhelmed when he comes face-to-face with his mother, Mary Winchester. Meanwhile, Sam fights for his life after Toni, from the Woman of Letters, shoots him
The Disappointments Room
The movie depicts the story of one family's terror-filled encounter within their own home. A mother and her young son move to a new house looking for a fresh start, only to release unimaginable horrors from its attic.
Friday, December 16, 2016
Samsung Note 2 - N7100 root and custom cwr
N7100 note 2
Root and Install custom CWR recovery
Download the package extract it
put note 2 in boot loader mode menu+vol up+power
plug it to cable open odin
click ap button from same folder select root file and flash
after restart again place it in bootloader
now select recovery tar from folder and flash it
Enjoy.... tested on N7100 note 2 other version please google first im not responsible for any damage to your device dont run it on vitnam or copy versions
Root and Install custom CWR recovery
Download the package extract it
put note 2 in boot loader mode menu+vol up+power
plug it to cable open odin
click ap button from same folder select root file and flash
after restart again place it in bootloader
now select recovery tar from folder and flash it
Enjoy.... tested on N7100 note 2 other version please google first im not responsible for any damage to your device dont run it on vitnam or copy versions
Wednesday, December 14, 2016
Monday, December 12, 2016
Mtk6580 CyanogenMod 12.1 Rom
Today Cm12.1 Final V3 For Our Primo GH5Mini......!
Rom ScreenShort:

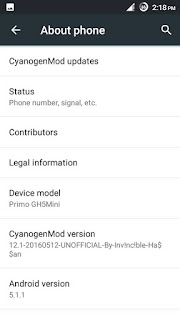
Rom Download Link: Click Now
Google Apps : Click Now
Root Tools : Click Now
Instructions For TWRP Recovery(Recommend):
1. Place ROM zip File in Your SD Card
2. Reboot in Recovery Mode & Go To Wipe Menu,Then Full Format Your Phone Storage.Like System/Data/Cache.
3. Then Go Back, Install zip From SD Card & Select The Rom,Then Flash Other Files.
4. Reboot & Enjoy........
Rom ScreenShort:


Rom Download Link: Click Now
Google Apps : Click Now
Root Tools : Click Now
Instructions For TWRP Recovery(Recommend):
1. Place ROM zip File in Your SD Card
2. Reboot in Recovery Mode & Go To Wipe Menu,Then Full Format Your Phone Storage.Like System/Data/Cache.
3. Then Go Back, Install zip From SD Card & Select The Rom,Then Flash Other Files.
4. Reboot & Enjoy........
Wednesday, December 7, 2016
Ouija: Origin of Evil (2016)
Set in 1967 Los Angeles, the movie tells the horrific story of a widowed fortune teller who decides to incorporate a Ouija board into her fake routine, but soon the board starts calling to her daughter, and all heck breaks loose.
Thursday, December 1, 2016
Triple 9
In TRIPLE 9, a crew of dirty cops is blackmailed by the Russian mob to execute a virtually impossible heist. The only way to pull it off is to manufacture a 999, police code for "officer down". Their plan is turned upside down when the unsuspecting watch what happen when plan A fail and no Plan B
The Hurt Locker
An intense portrayal of elite soldiers who have one of the most dangerous jobs in the world: disarming bombs in the heat of combat. When a new sergeant, James, takes over a highly trained bomb disposal team amidst violent conflict, he surprises his ...
i never seen this movie before or its tittle but today i found play it it seems nice 6 awards win rating 8.0 US army based film i recommend you should watch this
Nokia X2-1013 lolipop mod
lolipop mode for nokia
X2 - 1013
tested and working install custom recovery after root
trwp 2 plus
then install custom recovery
Download the package install it from recovery
X2 - 1013
tested and working install custom recovery after root
trwp 2 plus
then install custom recovery
Download the package install it from recovery
Tuesday, November 29, 2016
The Accountant (2016) HD
Christian Wolff is a math savante with more affinity for numbers than people. Behind the cover of a small-town CPA office, he works as a freelance accountant for some of the world’s most dangerous criminal organizations. With the Treasury Department’s Crime Enforcement Division, run by Ray King, starting to close in, Christian takes on a legitimate client: a state-of-the-art robotics company where an accounting clerk has discovered a discrepancy involving millions of dollars. But as Christian uncooks the books and gets closer to the truth, it is the body count that starts to rise.
Saturday, November 26, 2016
Masterminds - HD
The movie follows David Ghantt (Zach Galifianakis) as he is lured by a his crush and her mastermind friend to join one of the biggest bank heists in American history: the inside-job robbery of an armored car filled with $17 million in Loomis Fargo money.
Boo! A Madea Halloween (cam)
Cranky, fast-talking Madea (Tyler Perry) finds herself under attack and on the run from an assortment of ghosts, ghouls and zombies while keeping a watchful eye on a group of misbehaving teens. funny movie rating is 8.0 cam edition version
Friday, November 25, 2016
Awareness on Online Banking Cyber Crime
Computer crime has been defined as “any illegal unethical or unauthorized behavior involving automatic processing or transmission of data”.
Types of Cyber Crime
Phishing
 Very high is the number of phishing attacks against financial institutions, especially banks. What cyber criminals are after are, of course, all types of sensitive information such as account credentials, transfer history etc.A classic phishing attack consists in tricking the user into divulging personal banking data through fake emails. Attackers direct the recipient to a replicated website looking like the real bank site and encourage them to “login” or submit their information via ad hoc forms.APWG Global Phishing Survey reports that almost half of 2012 phishing attacks targeted shared hosting spaces as cyber criminals seek large scale phishing attack opportunities.
Very high is the number of phishing attacks against financial institutions, especially banks. What cyber criminals are after are, of course, all types of sensitive information such as account credentials, transfer history etc.A classic phishing attack consists in tricking the user into divulging personal banking data through fake emails. Attackers direct the recipient to a replicated website looking like the real bank site and encourage them to “login” or submit their information via ad hoc forms.APWG Global Phishing Survey reports that almost half of 2012 phishing attacks targeted shared hosting spaces as cyber criminals seek large scale phishing attack opportunities. Pierluigi Paganini of Infosec Institute advocates prevention is better than curing in this case, and suggests a few guidelines to fight the phenomenon:
Pierluigi Paganini of Infosec Institute advocates prevention is better than curing in this case, and suggests a few guidelines to fight the phenomenon:- Verify online accounts regularly;
- Never divulge personal information via phone or on insecure websites;
- Don’t click on links, download files, or email attachments from unknown senders;
- Beware of pop-ups. Never enter personal information in a pop-up screen.
 Very high is the number of phishing attacks against financial institutions, especially banks. What cyber criminals are after are, of course, all types of sensitive information such as account credentials, transfer history etc.
Very high is the number of phishing attacks against financial institutions, especially banks. What cyber criminals are after are, of course, all types of sensitive information such as account credentials, transfer history etc. Pierluigi Paganini of Infosec Institute advocates prevention is better than curing in this case, and suggests a few guidelines to fight the phenomenon:
Pierluigi Paganini of Infosec Institute advocates prevention is better than curing in this case, and suggests a few guidelines to fight the phenomenon:Watering hole
Watering hole cyber crime is an evolution of phishing. Instead of trying to convince users to visit a certain website, this technique involves injecting malicious code onto specific web pages, and waiting for visitors to be “infected”. Exploit kits to compromise websites are available in the black market.“Targeting a specific website is much more difficult than merely locating websites that contain a vulnerability. The attacker has to research and probe for a weakness on the chosen website. Indeed, in watering hole attacks, the attackers may compromise. Once compromised, the attackers periodically connect to the website to ensure that they still have access”
A famous watering hole attack is the one against South Korean banks happened in March 2013. Most banks had to interrupt their service due to data loss and servers issues, costing them millions and reputation damage.
“Targeting a specific website is much more difficult than merely locating websites that contain a vulnerability. The attacker has to research and probe for a weakness on the chosen website. Indeed, in watering hole attacks, the attackers may compromise. Once compromised, the attackers periodically connect to the website to ensure that they still have access”
Pharming
 What happens when cyber criminals want to target more web savvy users? Preventing is better than curing, but sometimes criminal techniques are just too advanced for 99.9% of online banking users. Pharming (from “farming” and “phishing”) is based on banks’ URL hijacking: when people try to enter their actual bank site, a redirection to another site occurs (see Palizine diagram).Experts say it’s one of the most difficult and advanced cyber crime techniques, but still possible via:
What happens when cyber criminals want to target more web savvy users? Preventing is better than curing, but sometimes criminal techniques are just too advanced for 99.9% of online banking users. Pharming (from “farming” and “phishing”) is based on banks’ URL hijacking: when people try to enter their actual bank site, a redirection to another site occurs (see Palizine diagram).Experts say it’s one of the most difficult and advanced cyber crime techniques, but still possible via:- DNS Cache Poisoning
- Hosts File Modification

Credit card redirection
The nightmare of ecommerce websites is the redirection of their users to domains managed by cyber attackers. Credit cards redirection allows criminals to steal money and sell precious sensitive information in the black market.
MITB: Man In The Browser
Online banking experts say this is a huge threat to banks and their clients. MITB is regarded as one of the most effective cyber crime strategies, and costed billions to banks all over the world in 2012 and 2013. A malware infects the browser of the victim, looking like a plugin, browser extension or Active-X control, and modifies online transactions to steal funds, without being detected. Here some of the most common trojans found:
Here some of the most common trojans found:- Zeus is spread via phishing schemes and used to acquire illegally bank credentials via MITB techniques. First detected 6 years ago, it attacked US government websites and despite FBI intervention and hundreds of millions in damage, it is still a menace for online banking professionals. Real time statistics on Zeus malware can be accessed at Zeus Tracker.
- Carberp is a famous bank account takeover malware which does not need admin authentication to be installed and therefore bypasses Windows security systems. The source code is leaked. Security industry experts say it’s a powerful menace to online banking.
- Sinowal is “a malicious application that allows hackers to remotely access you computer system letting them modify files, steal personal information and install more unwanted software” (AVG).
- Clampi has been around since 2008, affecting Microsoft computers and stealing from thousands of websites. SecureWorks regards Clampi as one of the most professional and profitable cyber crime operations of all times.

DDoS attacks
DDoS attacks represent another threat to online banking sites. Operation “Ababil” by Izz ad-Din al-Qassam Cyber Fighters hacktivists attacked top US banks such as U.S. Bankcorp, PNC, SunTrust, JPMorgan, and Bank of America. What’s unique about DDoS attacks is that it does not employ botnets, but rather volunteers, making it difficult to detect anomalous traffic and deal with the attack.
- Volume Based Attacks – The attacker tries to saturate the bandwidth of the target’s website by flooding it with a huge quantity of data.
- Protocol Attacks – The attacker’s goal is to saturate the target servers’ resources or those of intermediate communication equipment (e.g., load balancers) by exploiting network protocol flaws.
- Application Layer (Layer 7) Attacks – Designed to exhaust the resource limits of web services, application layer attacks target specific web applications, flooding them with a huge quantity of HTTP requests that saturate a target’s resource
Prevention of Cyber Crime
- Avoid disclosing your identity to any strangers.
- Always use latest antivirus software to guard against virus attacks.
- Never send your credit card number to any site which is not secured.
- Use of firewall
- Change passwords frequently
- Uninstall unnecessary software

Prevention of Cyber Crime
- Avoid disclosing your identity to any strangers.
- Always use latest antivirus software to guard against virus attacks.
- Never send your credit card number to any site which is not secured.
- Use of firewall
- Change passwords frequently
- Uninstall unnecessary software
Dot CHK recovery
hi today i am gonna show you how to recover your file that got infected by virus and name as chk cant be open or found
here is the very easy trick to do this without paying any charges at all, just need to download the package extract it as usual using winrar there are two applications that i place in this rar just open it access your infected file recover it.
tested and work for me so try it
Download
here is the very easy trick to do this without paying any charges at all, just need to download the package extract it as usual using winrar there are two applications that i place in this rar just open it access your infected file recover it.
tested and work for me so try it
Download
Thursday, November 24, 2016
Hunting Hitler
most of the people believe that Adlof Hitler wont die in the bunker in 1945 he got escape from that bunker by spiking Russian army, after 70 year USA top class men try to search for hitler that where he did actually run they nrearly found him in Spain and Argentine but question is still there, no dead body yet found no DNA match a super power of German's called Nazi let him safe path even after the end of 2 world war which he actually field to win so many question's so much to do FBI Mi reports nothing yet have clear idea watch season one episode one HD Quality
Watch Online
Watch Online
Wednesday, November 23, 2016
Some crazy things (IOS) Siri can do !
With the release of iOS 10, Apple has again improved and expanded the capabilities of Siri, the built-in “digital assistant” feature that lets you control your iPhone and iPad with your voice.
For many people though, Siri still seems to be relegated to the “party trick” category—it’s fun to play around with (Hey Siri, tell me a joke! Hey Siri, beam me up! Hey Siri, beatbox!), but not many people seem to use it as part of their daily workflow for anything productive.
However, with the recent enhancements to Siri’s accuracy in voice recognition and abilities, using your voice really can help you save time and keep you organized. Here are six ways Siri can help.
Control Third-party Apps
One of the most significant enhancements to Siri in iOS 10 is the ability it now gives you to control third-party apps with your voice, often without even having to open the actual app. Since the release of iOS 10, developers have been rolling out updates to their apps, touting “Siri integration.”
To see which apps on your device support this, go to Settings > Siri > App Support.
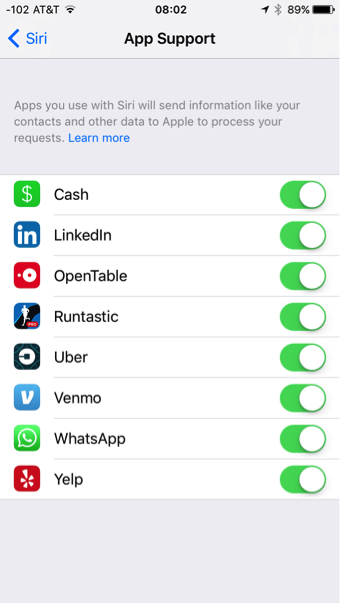
Siri-integrated apps currently fall into the categories of messaging (for example, WhatsApp), money transfer (Venmo), workouts (Runtastic), ride hailing (Uber), photo searching (Pinterest) and audio/video calling (Skype). Switch on any of the apps you see listed in App Support settings to enabled Siri control. You can also go to the App Store on your device and search for “Siri” to find additional apps to install.
Once enabled, you can start using these apps with Siri by telling it what you want to do, and in which app. For example, hold down the Home button on your device, and say something like, “Call me an Uber.”
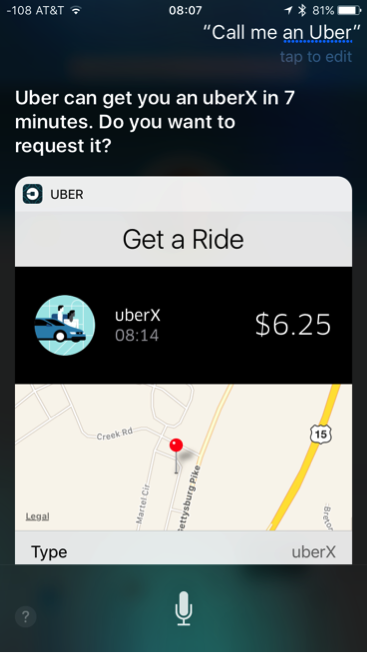
Siri will tell you how soon a car can arrive to pick you up and ask if you want to confirm it. Some examples of things you can say with other apps include, “Start a workout in Strava,” or “Send a message to Nick through LinkedIn,” or, if you have the OpenTable app installed, “Find me a reservation for two at 7PM at an Italian restaurant.”
Depending on the app, you may have to experiment a bit to find out exactly what you can ask Siri to do with it, but if an app has Siri integration, it’s worth playing around to see how using your voice might save you some time.
Quickly Access Settings
The Settings app in iOS 10 has gotten denser, and Apple has also shifted the location of certain settings around, so it’s not always the easiest thing to navigate through the menus-within-menus to find the settings you want to view or change. Instead of hunting around, just ask Siri to open the settings you want. For example, hold the Home button and say, “Open Mail settings,” or “Open Keyboard settings,” or even “Open Siri settings.”
Siri also recognizes when you’re using a third-party app. For example, if you’re using the LinkedIn app and say, “Open Settings,” the LinkedIn settings will pop open, without you having to press the Home button to leave the app, tap settings, and scroll down to LinkedIn settings manually.
Teach Siri About Your Relationships
Siri can already search through your Contacts when you call out people by name with commands like, “Send an email to Nick Brazzi,” or “Call Jess Stratton,” but you can also teach Siri about your family and work relationships, so you can start saying things like, “Call my brother,” or “Start a FaceTime video call with my dad.”
To set this up, go into the Contacts app and find your own contact card. Tap the Edit button and scroll down and look for the field labeled, “Add Related name.” Choose the relationship for the person you have in mind.
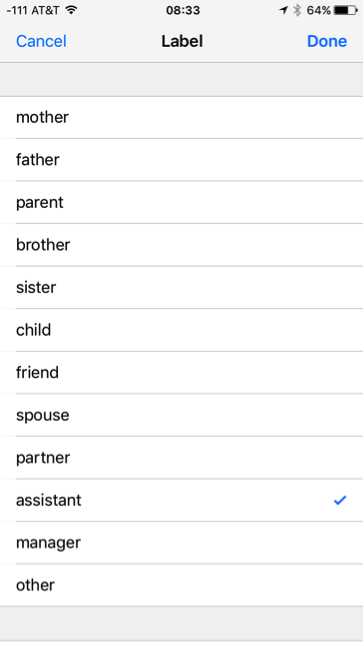
Then tap the field next to the new label to choose the person in your contacts this label applies to. Repeat this for any other person you’d like to refer to by their relationship to you.
Then tap Done, and go to Settings > Siri, and in the My Info field, make sure your own contact info is selected. Siri will now understand the relationships you’ve set up and you can start saying things like, “Add a meeting with my manager this Thursday at 2pm.”
Create Reminders for Messages, emails and more
More and more these days, important information or requests may be sent to you via text message. But in the Messages app, there’s no way to mark an individual message as important, or to create any kind of reminder to respond to the message later.
Siri can help you out though. When you receive an important message, hold town the Home button and say, “Remind me about this.”
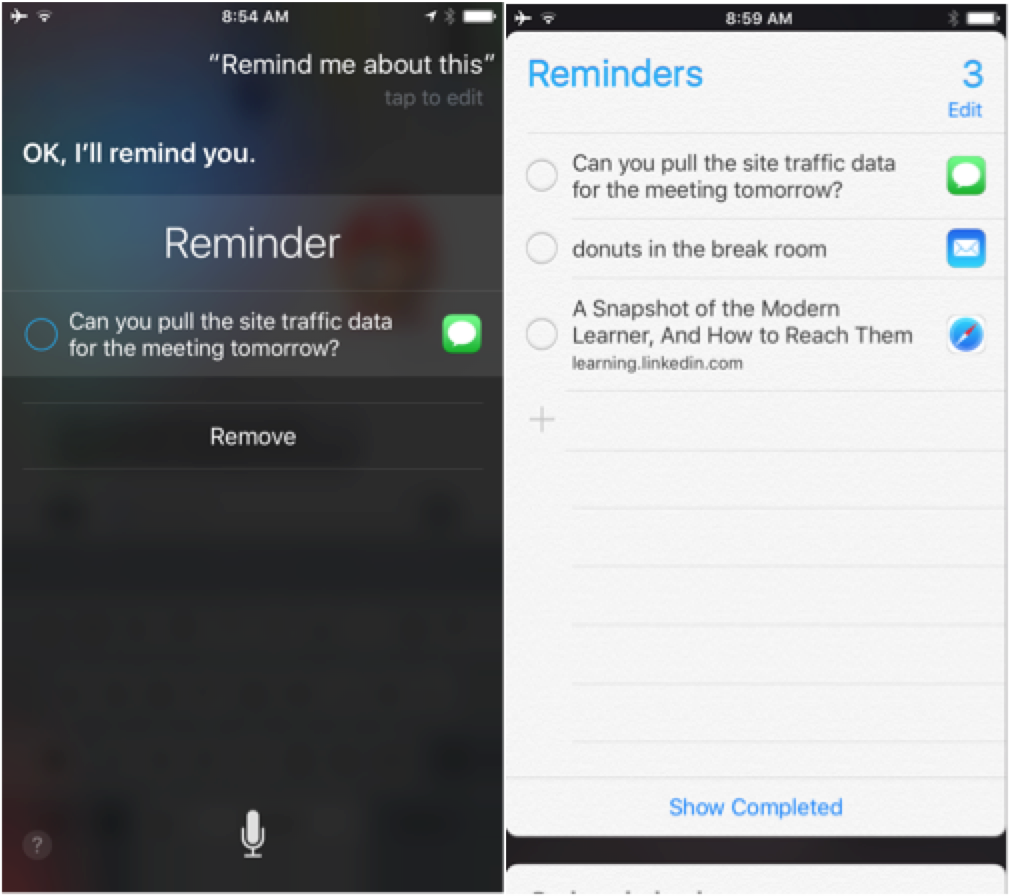
Siri automatically generates an item in the Reminder app. You can tell Siri to remind you about emails and webpages too. Each item will show up in the Reminder app, and you can tap the app icon next to the reminder to jump back to that app and view the item.
You can even tell Siri to remind you about these items at specific times, for example, say “Remind me about this in an hour,” and you’ll get a notification when that time arrives.
Make Siri Use the Search Engine of Your Choice
Siri’s default search engine is bing.com, so if you ask something like, “How do you repair a broken hard drive,” the results you see will be bing results. If you want to change search engines, just call them out by name.
Say, “Search google for how to create a pivot table,” or “Search yahoo for how to set tab stops in Word.” You can even ask Siri to search Wikipedia: “Search Wikipedia for Artificial Intelligence.”
Have Siri Do the Math
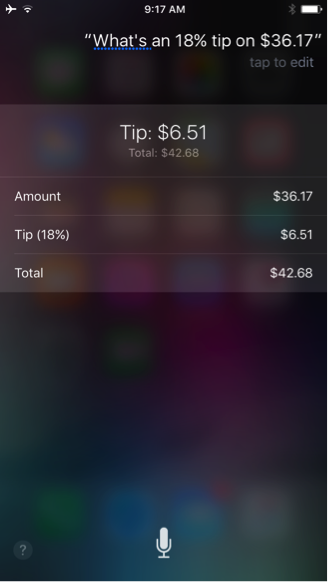
The next time you need to perform a calculation, instead of opening the calculator app, for a quicker answer just ask Siri: “How many tablespoons in half a cup?” or “What’s an 18% tip on $36.17?” or “What’s 1/3 of ¾?” Siri will have the answer for you in a second or two.
This is just a small sampling of some ways Siri can help you be more efficient and productive. For ideas on more things Siri can do for you, you can ask Siri itself by saying, “What can you do,” and you’ll be provided a long list of other commands you can make use of.
Monday, November 21, 2016
Supernatural Season 12 - Episode 06: Celebrating The Life Of Asa Fox
Season 12 begins with Dean becoming overwhelmed when he comes face-to-face with his mother, Mary Winchester. Meanwhile, Sam fights for his life after Toni, from the Woman of Letters, shoots him.
after killing a copy Hitler dont know why they are against hitler he just end Jewish lobby American are Jewish or cristan the season it taking again a turn that people decide to watch it again
Fantastic Beast and Where To Find Them
In 1926, Newt Scamander arrives in New York by boat, carrying a mysterious suitcase that is home to dozens of magical creatures. However, some fantastic beasts escape, which could spell trouble for both the wizarding and No-Maj worlds.
After the success of hairy porter this film has been launched on the cinemas witches and beast try to tackle the world but actually they try to save the world the bad character is itself a big name after cracking him down i think next part would be much more amazing one rating is 8 i can gave it 8.5 for great cast and brilliant idea's
cam recording not that great but still can watch till HD
Hardware
The film centers on Mo who is a cyborg comes from an extraordinary world. He tries to collect robot parts and rebuild them to create an army for fatal battle.
i should recommend to watch this
Inferno (cam edition)
When Robert Langdon wakes up in an Italian, with no memory of what has transpired over the last few days, he teams up with Dr. Sienna Brooks. Together, they race across Europe and against the clock to stop a madman from unleashing a global virus that would wipe out half of the world’s population.
Sunday, November 20, 2016
cybercafe pro 5 with crack
CyberCafePro Downloads
CyberCafePro is a very secure software package but unfortunately it has to play within the restriction and rules of the operating system. This can cause security holes but luckily this security hole is very easy to fix.
CyberCafePro is free Internet Cafe Software.
Download & then install the CyberCafePro Server software to the computer which will be used as the front-desk or Main Control Station, download & then install the CyberCafePro Client software to ALL the computers which will be used by customers.
Note: Please install the CyberCafePro Server software before the CyberCafePro Client software (Install Client software on computers other than the Server).
CyberCafePro is a very secure software package but unfortunately it has to play within the restriction and rules of the operating system. This can cause security holes but luckily this security hole is very easy to fix.
CyberCafePro is free Internet Cafe Software.
Download & then install the CyberCafePro Server software to the computer which will be used as the front-desk or Main Control Station, download & then install the CyberCafePro Client software to ALL the computers which will be used by customers.
Note: Please install the CyberCafePro Server software before the CyberCafePro Client software (Install Client software on computers other than the Server).
Download server and Client setup extract them install server on server pc and crack it from cracker turn off antivirus while cracking coz it will damage the file
install Client ver on clients
after that start user or time code make setting adjustments and backup using tutorial video
Friday, November 18, 2016
Iron Man 3
Marvel’s “Iron Man 3” pits brash-but-brilliant industrialist Tony Stark/Iron Man against an enemy whose reach knows no bounds. When Stark finds his personal world destroyed at his enemy’s hands, he embarks on a harrowing quest to find those responsible. This journey, at every turn, will test his mettle. With his back against the wall, Stark is left to survive by his own devices, relying on his ingenuity and instincts to protect those closest to him.
Iron Man 2
With the world now aware of his dual life as the armored superhero Iron Man, billionaire inventor Tony Stark faces pressure from the government, the press, and the public to share his technology with the military. Unwilling to let go of his invention, Stark, along with Pepper Potts, and James “Rhodey” Rhodes at his side, must forge new alliances – and confront powerful enemies.
man who build a suit to kill bad people and provide justice but he wont done it well
Tuesday, November 15, 2016
Angels And Demons
a story that resembles the tv series that got so hit supernatural killing daemons and angles typical american story as we all know angel and daemon are exist but they never been shown or you cant kill them all whats so ever
Watch Online
Watch Online
Subscribe to:
Posts (Atom)








































